Reimagining fast, secure digital transformation for your enterprise.
Our innovative approach to digital transformation will speed the security maturation process for any corporate enterprise or government agency. We identify critical impacts to applications and provide complete security coverage across the full stack of multi-cloud and enterprise environments.
CUSTOMERS
Trusted by great organizations.
Protek Government has delivered hundreds of successful IT solutions for scores of government clients. Here are just a few of the government agencies we’ve helped with complex digital transformations.
ALL-IN-ONE PLATFORM
Functionality, performance, security across enterprise and cloud environments.
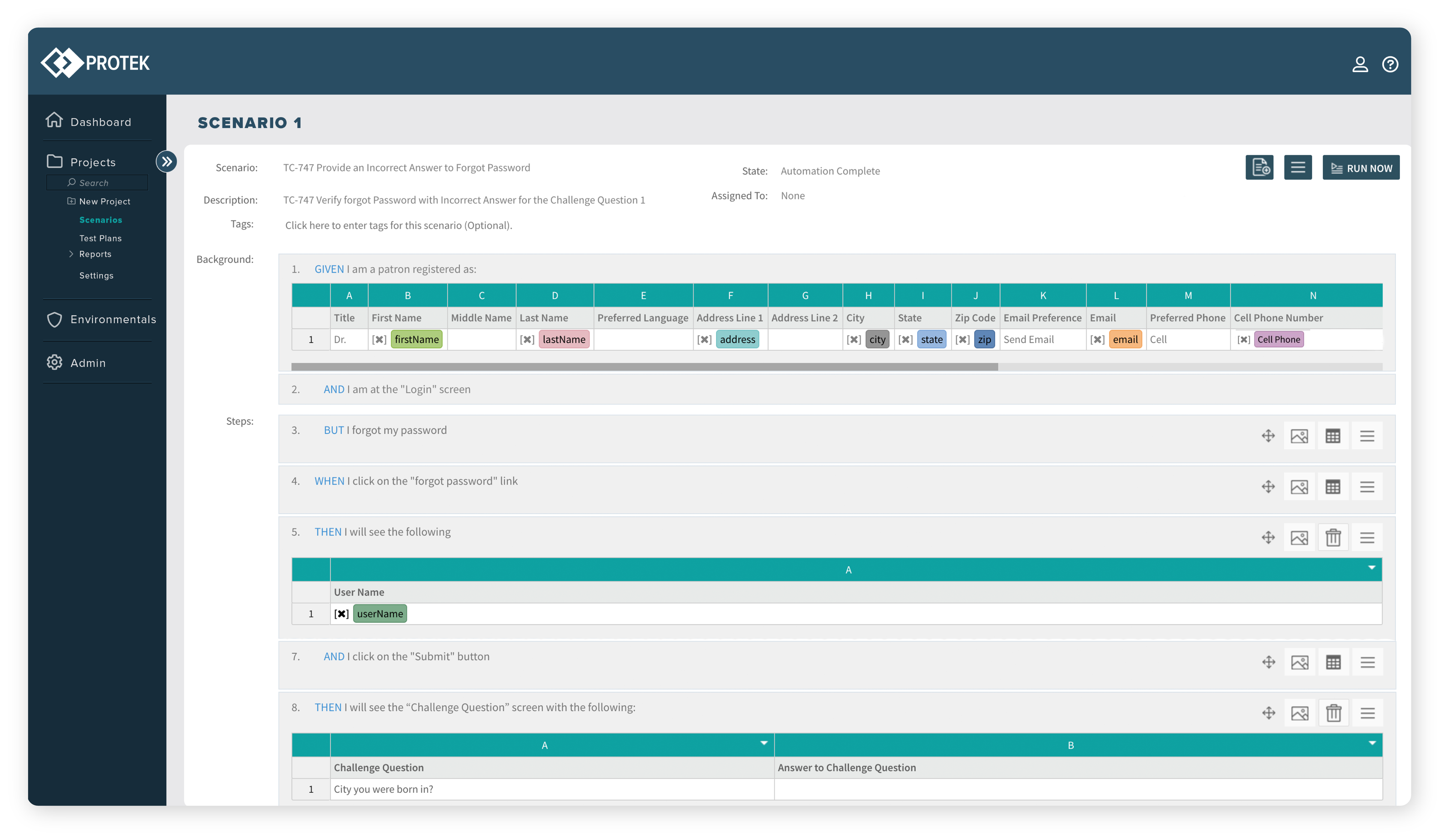
We author test cases in plain English to define your application-user interactions (Scenarios). Then we automate these scenarios to validate that your systems do what they are intended to do.
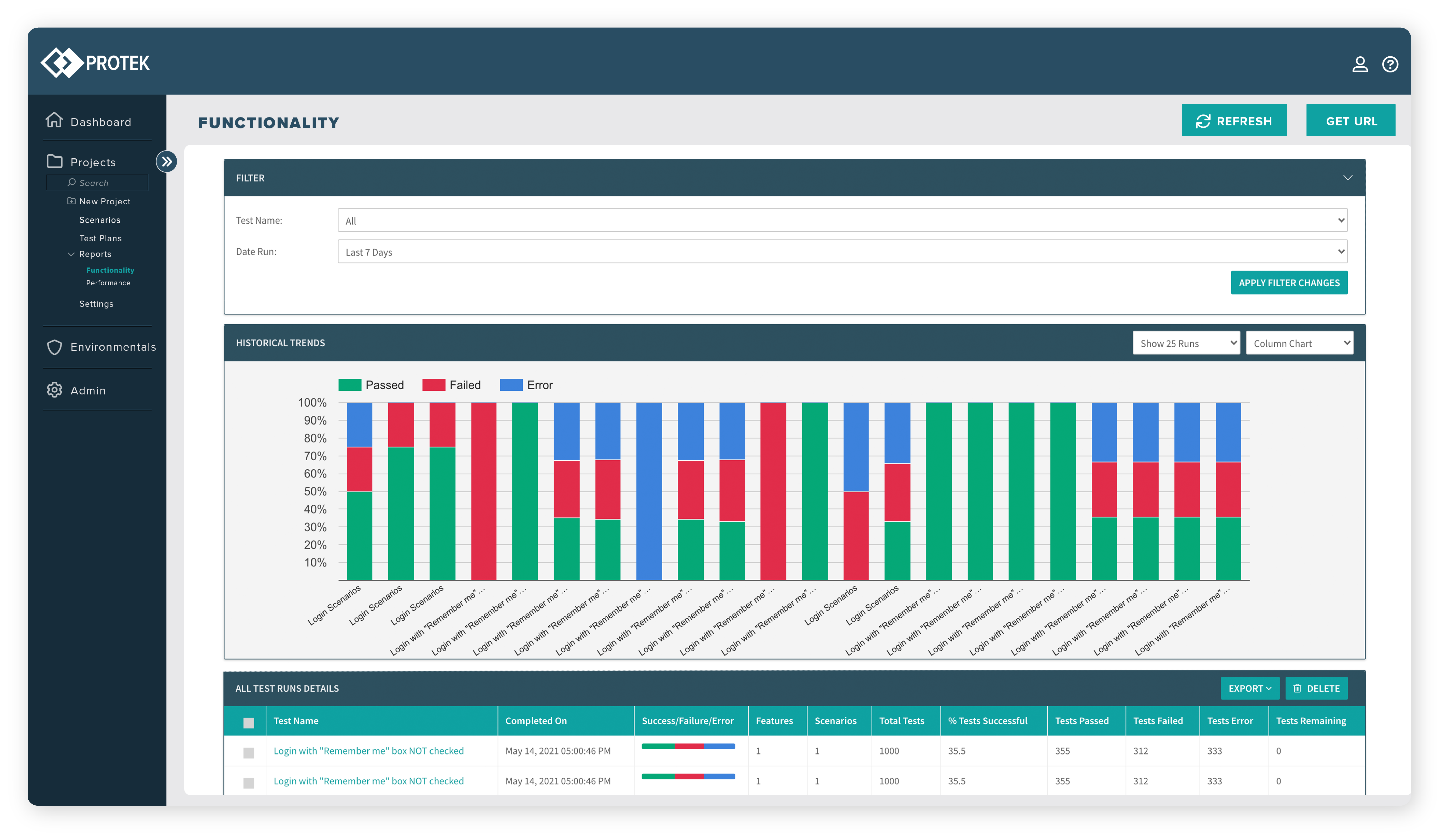 Run thousands of test cases in parallel
Run thousands of test cases in parallel
Running automated scenarios in parallel cuts the execution time to test your applications. Our process takes only a fraction of the time of other automation engines, giving you much greater speed to value. Test as you go
Test each Scenario as soon as it is built to validate that it works as designed. Test early and often, in any environment (dev, test, UAT), to find and eliminate issues quickly. Integrate into existing bug-tracking/workflow systems
Breakpoint integrates with most bug reporting and tracking systems, including Jira and Azure DevOps, to automatically create and populate bug tickets. Regress every day without human intervention
Run all tests daily to find and fix regression issues, especially when you add new functionality.
Automate any layer
Go beyond UI testing and test any layer with almost any interface, including REST/SOAP endpoints, S/FTP interfaces, raw socket connections, and more.
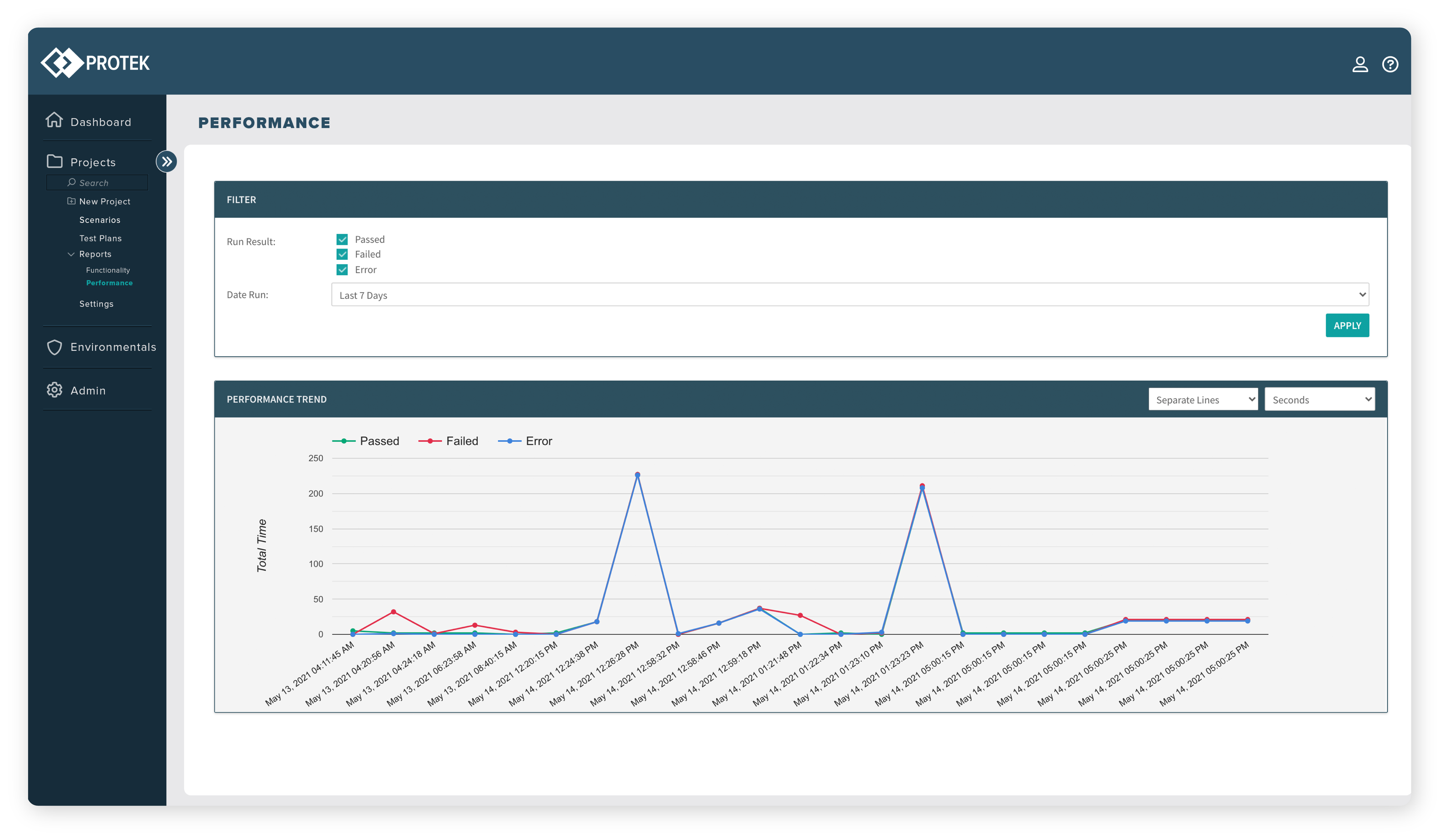 Validate application functionality
Validate application functionality
Ratchet up the load on your systems to:
- Assess if functionality works as intended under load
- Determine if system performance is consistent or degrades
- Find the load breaking point — how many simultaneous users will crash your system?
Test under different loads to validate if your functionality behaves consistently with varying numbers of simultaneous users. Validate robustness
Find your system's breaking point and validate that it is at or beyond your expected usage. Track performance
See performance stability or degradation as your applications approach and exceed maximum load.
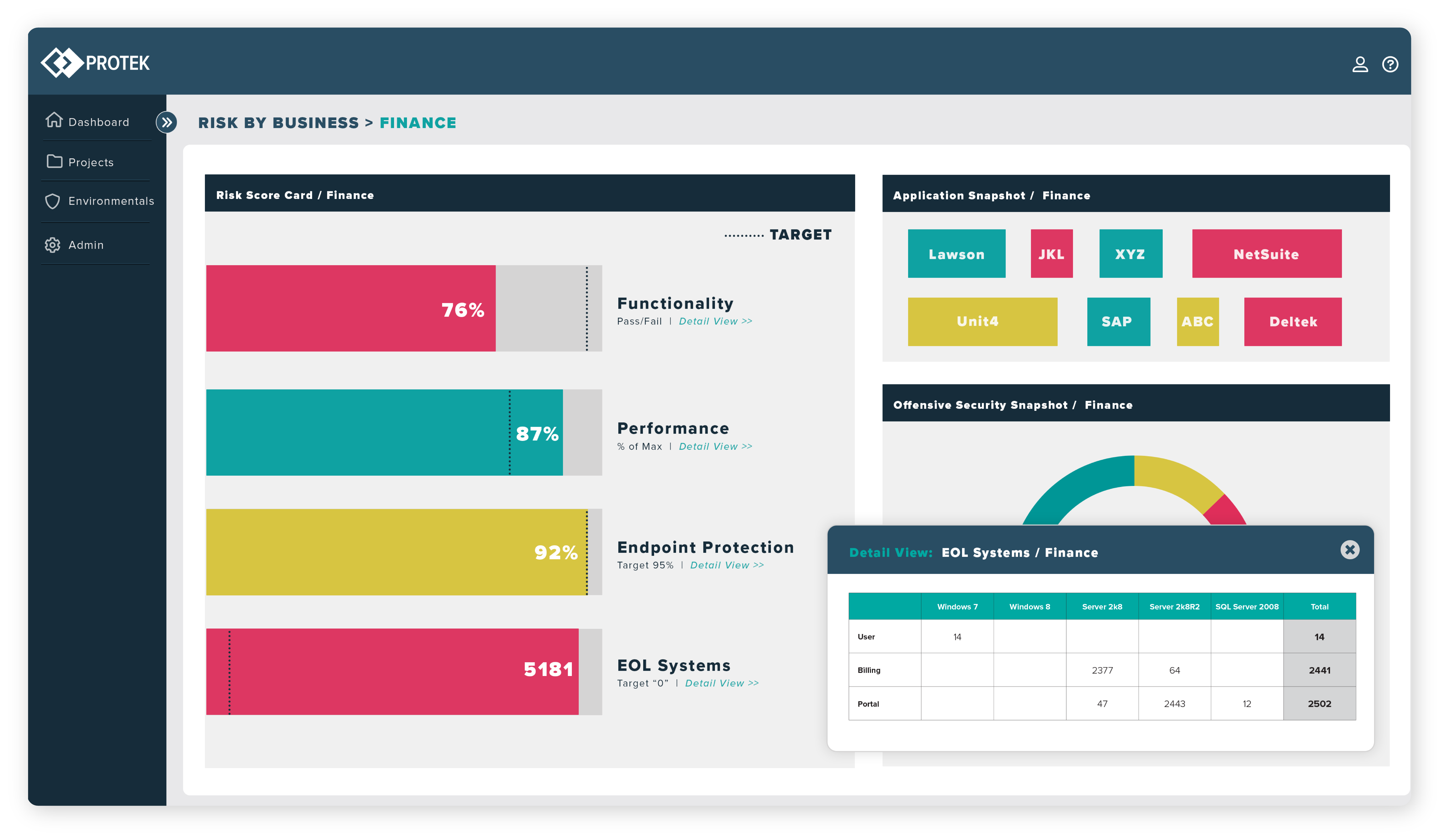 Find runtime vulnerabilities
Find runtime vulnerabilities
Uncover runtime vulnerabilities that may only appear when your system is near, at, or beyond maximum load. Define security expectations
Author security Scenarios that test for various types of penetration. Proactively find runtime security vulnerabilities
Assess if your applications are susceptible to runtime security vulnerabilities as you progress through different environments. Find and eliminate vulnerabilities to seal critical gaps before deploying to production.
Breakpoint can create new data on each test execution to eliminate the need for repetitive and time-consuming efforts to generate test data, perform data entry and prepare test data. Automate once and execute in any environment
Execute tests in any environment, even environments that have previously been off-limits, including pre-prod and even production environments to ensure new functionality will work securely at load when you go live.
Improve security across your environment.
DEFENSIVE SECURITY
Maximize your existing security technology investment. Surface risk conditions that often go unnoticed in cloud and enterprise environments. Our Endpoint Defense Program hardens and protects your critical systems from emerging threats that could disrupt your business operations and applications.
Identify endpoint assets across all environments
Catalog and report the status of all endpoints within your enterprise environment to understand what needs to be protected.
Implement endpoint protective technologies and standards
Implement, manage, and maintain endpoint protective technologies and OS-hardening standards for managed endpoint assets (on-premise, remote, or hosted).
Continuously monitor networks for rogue assets and nonstandard configurations
Detect unmanaged and noncompliant systems and report on remediation actions to reduce operational risks across your technology footprint.
Gain incident insights and endpoint security recommendations
Benefit from incident analyses to help your security operations and response teams and improve your MTTR. Our reporting and recommendations will help you improve your endpoint security.
Deploy and configure endpoint security controls
Automate the deployment and configuration of endpoint security technologies. Recovery activity analysis and reporting will ensure that follow-up actions do not inadvertently introduce new environmental risks.
OFFENSIVE SECURITY
Take an adversarial approach — without the risk. Reduce the attack surface of your cloud and enterprise systems by passively identifying conditions that an attacker could exploit to access your critical assets. Armed with system, identity, and vulnerability intelligence, our Protek Government platform identifies and prioritizes risks without the need for traditional technical testing.
Perform continuous passive reconnaissance across all enterprise environments
Inventory and analyze the vulnerabilities of your active assets across the cloud and enterprise. Identify high-value user accounts and user groups that attackers can exploit.
Identify coverage gaps in endpoint security technologies
Identify coverage gaps and system vulnerabilities across endpoint assets in your cloud and enterprise environments without technical testing, to avoid potential system outages. Identify user accounts and security groups that warrant additional monitoring and identity control measures.
Display the attack paths most likely to compromise your critical business applications
Take an adversarial approach to understand the most likely attack paths available to external and internal attackers. Improve how your IT and security teams prioritize patching and vulnerability remediation based on asset value and ease of exploitability.
What you can accomplish in 24 hours.
Within 24 hours of deploying our solution, you will identify gaps in your endpoint security coverage and develop an adversarial model to identify pathways that can be exploited to harm your critical business systems and applications.
With your vulnerabilities prioritized by value and exploitability, your technical teams can take immediate action where it counts, and greatly reduce your attack surface.




